What are the signs that your site has been compromised?
Several signs indicate your site has been compromised:
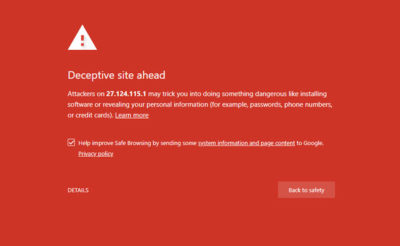
a) Site blacklisted by Google (or other search engines)
If Google detects that your website contains malware, it will report it with a red page “Deceptive site ahead” or “The site you are about to visit contains malicious programs” when you try to visit your site.
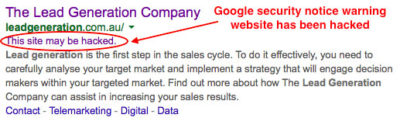
b) Message in Google search results (compromised site)
If Google detects that your site has been compromised, it may indicate it in the search results with a message “This site may be hacked”.
c) Google Search Console
If you have entered your site in the Google Search Console, in the section “Search traffic” > “Search analysis” you will find in the list of search queries from users, terms that have little to do with the topics of your site. For example, terms that are clearly spam, such as cialis, viagra, sex, online gambling, and many others.
d) New users in WordPress’s dashboard
A clear sign of compromise is finding new administrator users in the WordPress dashboard.
e) Page with the words “hacked” when you connect to your site
Defacement consists of changing the compromised site’s main page to a page that usually contains a threatening image along with the nickname of the hacker who comprmised the site.
Step-by-step procedure
1) Document facts in detail
In this first step, try to gather as much information as possible about the incident:
(a) Date and time when you became aware of the fact.
b) What is the element that made you discover the compromise of your site (for example if the main page of your site has been replaced by another, in that case make a “screenshot” of the page and save it in a folder with all the documentation gathered)
c) Date and time you contacted your hosting provider and all the information you will be able to gather (phone calls, emails, etc.)
2) Make a scan of the compromised site
The second step is to scan the entire site looking for viruses or malware that may have been installed by the hacker to exploit the compromised server.
The scan can be performed:
a) If it is possible to login into the administration dashboard, use a security plugin (Wordfence, Sucuri, or others)
b) If it is not possible to login into the administration dashboard or you want to do a second scan, use a web-based scanner (Sucuri Site Check or Quttera)
3) Scan your computer
It often happens that the hacker manages to steal the credentials of access to the administration dashboard of WordPress thanks to a trojan virus installed on your computer.
It is therefore very important to make sure that your computer is not infected with viruses, trojans or backdoors. Use a professional antivirus software such as Bitdefender.
4) Inform your hosting server provider
The hosting provider can help in such cases, and it often happens that the hosting provider is the first to inform the site owner of the compromise.
Usually the hosting provider has a team of technicians trained in this type of event, who can help you solve the problem as quickly as possible.
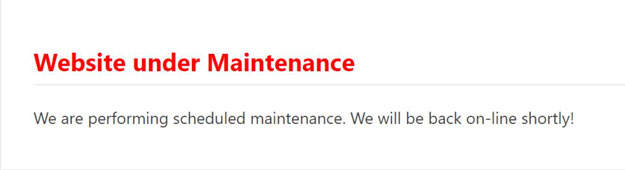
5) Putting your site under maintenance
At this point you have to put the site in a state of maintenance, to prevent any viruses or malware from infecting the computers of visitors to the site.
The easiest and fastest way is to enter the following code in your child’s theme functions.php file:
If everything works as expected, your website should display a message like this:
When you have finished cleaning up your site, simply delete the code you added in functions.php file.
6) Make a backup copy of your site (file + database)
It is advisable to make a backup even if the site is still infected, as it is the proof of the compromise, and it will help you in the next step where you will compare the files of the infected site with the original WordPress files that you will download. Using cPanel, select all the files on your site and compress them into a .ZIP file that you will download to your computer.
To save the database, use phpMyAdmin to create a dump of the database.
7) Delete any administrator users added by the hacker
It is important to block access to the WordPress administration dashboard by the intruder. Carefully check whether an administrator user has been added, in which case it should be deleted immediately.
If you do not have access to the WordPress dashboard, you can do it using phpMyAdmin via cPanel.
8) Change the passwords of all users/services related to the compromised site
a) Admin password
This is the first password you will need to change.
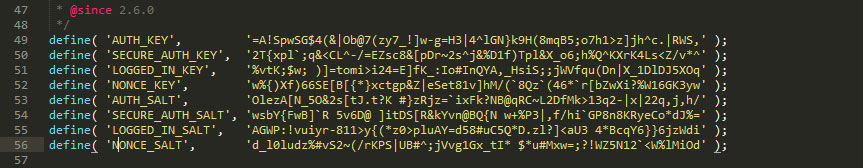
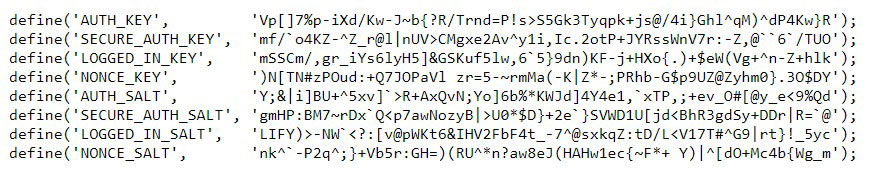
Before changing it, you should first change the “salt keys” of your site. Salt keys” are long strings of random characters in the WordPress configuration file, wp-config.php, which are used to encrypt passwords and cookies on your WordPress site.
The easiest way to change the “salt keys” is to connect to your hosting server through the cPanel administration panel, open the configuration file wp-config.php and replace the entire block of “salt keys” with unique strings created using the tool provided by WordPress.org (Salt Key Generator https://api.wordpress.org/secret-key/1.1/salt/ Note: at each refresh of the site page, a new unique set of strings is displayed).
Once you change the “salt keys”, login into the administration dashboard, and change the password of the administrator user.
Setup a secure password with at least 12 characters, including upper and lower case letters, numbers and symbols such as £$%@*§# (to set it automatically you can use a password generator such as Password Generator Plus https://passwordsgenerator.net/plus/).
If it is not possible to login into the administration dashboard, connect to your hosting server through cPanel, open phpMyAdmin, and in wp_users’ table, check that the e-mail address of the administrator user, corresponds to the address you set when you installed WordPress. If the administrator’s email address was changed by the hacker, reset it to the initial address.
Go to the login page (wp-login.php) and click on the “Forgotten password?” link to reset your password.
b) Other passwords
Once the password of the administrator has been changed, change the password of any other users, the password of the site’s database, cPanel’s password and finally the FTP or SSH passwords.
9) Malware removal
This is the most delicate and complex step of the whole procedure.
If you have access to the WordPress dashboard, you can install an antimalware plugin (Wordfence, Sucuri, or others) and scan the entire site for malware. Once the malware has been detected, you can delete it by clicking on the malware button.
If you do not have access to the dashboard, you should contact a WordPress security expert who can help you with malware removal and site’s cleanup!
10) Securing your website
Once the site has been cleaned up, and verified with a new scan using the services provided by Sucuri Site Check or Quttera, it is advisable to proceed with a systems hardening of your WordPress site.
11) Last tip!
After a WordPress site has been compromised, you should consider changing your hosting provider, this time choosing a provider that can provide you with a better security in terms of infrastructure and technical support.