Every year SplashData publishes the ranking of the worst passwords most used by users on the Internet.
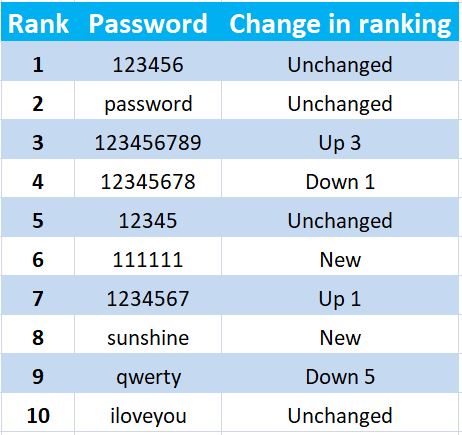
For the sixth consecutive year (2018) the most widely used password is “123456”.
Here is the ranking of the first 10 passwords taken from the 2018 ranking, with an indication of the changes in position in the ranking compared to the previous year’s ranking (2017).
Worst passwords 2018
Basic rules for creating and managing secure passwords
The basic rules to create and manage secure passwords are indeed 3:
- Using complex passwords
- Use different passwords for each site/service
- Change them regularly
1) Using complex passwords
As evidenced by the password classification provided by SplashData, many users, unaware of the risks they might face, often because of laziness or because they are not aware of suitable tools to create and manage complex passwords, prefer to use passwords that are easy to remember and that afterwards maybe they write down in a notebook or even worse on a “post-it” glued on their computer’s monitor!
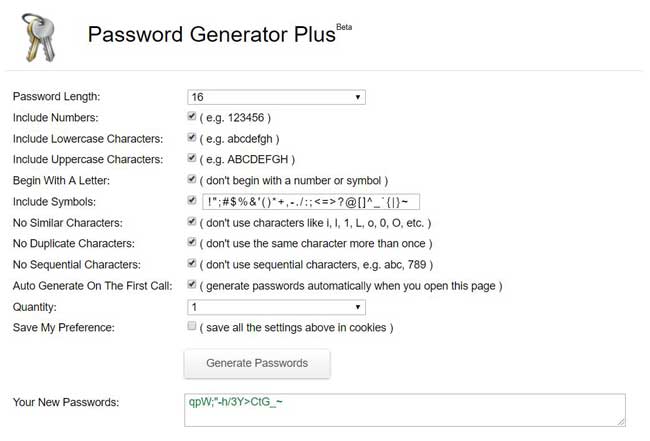
To solve the problem of creating complex passwords, there are “password generators” apps that, by setting a few parameters and clicking on a confirmation button, you can have random passwords each time different, to be used on websites and on any electronic device used to access remote services.
The password generating apps can be found either within password management software or in online Internet sites.
In this last category, there are two excellent sites : RoboForm and Password Generator Plus.
2) Use different passwords
In addition to using weak passwords, another mistake that is often made is to use the same password for multiple sites or services on the Internet.
Also in this case, the best solution is to use a password manager app that allows you to save all passwords in a single program where you can classify and organize all your passwords.
The password archive is protected by a single password (“master password”), and the entire archive is further protected by strong encryption (AES-256 or similar).
The archive can then be saved on your computer’s hard disk or on a remote cloud server .
Between both options, the safest is saving it on a local computer.
If you prefer to use a cloud service, it is always safer to use a private system, i.e. not accessible to users who are not part of your organization.
If you cannot use a private cloud system (higher costs) and you have to use a public service (Dropbox, Google Drive or similar), it is advisable to add an additional layer of protection, encrypting the password archive with an “end-to-end encryption” software such as Tresorit, Sookasa, Boxcryptor or similar.
3) Change passwords regularly
The last rule is that you need to change your passwords at regular intervals, changing them more often on high-critical systems (containing sensitive data).
Also in this case, password management apps are useful, where many of them have features that allow the setting of rules to force users to change their passwords at set intervals.
WordPress and user password management
Considering that WordPress is a Web-based system that also offers the possibility for various users to access the administration dashboard, the 3 rules above, must be applied in a precise and systematic manner.
To facilitate this task, there are a few plugins that provide a number of features to help site administrators set up password management rules based on the different users’ roles in a WordPress site.
A good plugin that I recommend is Password Policy Manager for WordPress (more information on the developer’s website WP WhiteSecurity).
How to check if your passwords have been compromised
During system hacking, attackers aim to obtain users’ personal data, so to use it for spam campaigns, for access to confidential systems (in the event that user passwords are stolen) or in the most extreme cases for identity theft.
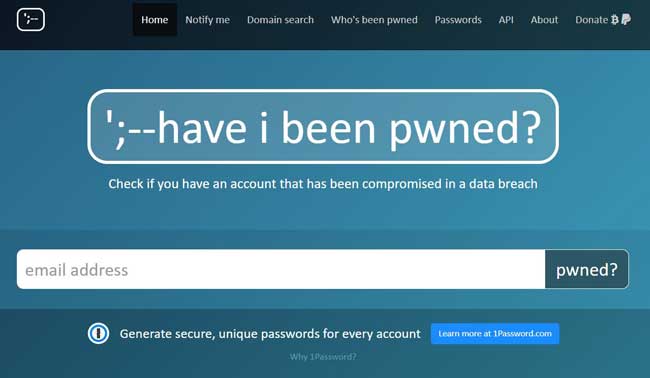
Troy Hunt, an American computer security expert, provides an excellent service through his website “Have I Been Pwned” where he keeps track of all the thefts of personal data that have occurred in recent years against many Internet sites.
The site offers the possibility to verify if an email address has been compromised or not.
To verify just go to the homepage of his site, enter the email address and click on the button “pwned?”.
If nothing is found in the archives, the phrase “Good news – no pwnage found!” on a green background will be displayed on the same homepage.
Otherwise you will see the phrase “Oh no – pwned!” on a red background, and the list of compromises in the archive of the site where the email address was found.
It is also possible to lookup for a whole email domain (useful for businesses) on the page Domain Search which can only be performed after a check of the actual ownership of the same domain.
Finally, you can register on the site (Notify Me) to receive a notification if your email or domain are found in a future data breach.