Remember the comic strip Lucky Luke, the fastest gun in the Far West?
He shot faster than his shadow!
That’s the image that came to my mind when yesterday afternoon I received an alert coming from the Sucuri security plugin, reporting an unusual file inside one of my client’s website.
Unsure about the name of the file (.query.php) and by its characteristics (hidden file and saved in the wp-includes folder), I SSHed into the server, to check the content of the file…
surprise!!! 🙂
A remote PHP shell…
I immediately contacted the IT manager of the client’s company, to ask for an explanation, since they had installed both the virtual server (VPS) and WordPress.
The sysadmin, a bit disappointed, assured me that the installation had been performed according to established guidelines and that it was impossible that the site had been hacked, since the virtual server had just been created, installing the usual operating system (Ubuntu 20.04) with the usual security guidelines, and that WordPress had been installed automatically, using the latest release (5.9.2) that there was no plugin installed and was using the basic theme 2022… How is it possible that the site had been hacked?!
The game was getting more and more intricate….
The only way to find out was to look at the web server log’s file (Nginx in this case) and look for any signs of compromise!
Et voilà!!
Analysis of attack
Let’s look at each step in detail:
1) “GET /wp-admin/install.php HTTP/1.1” 200 13315 “-” “curl/7.74.0”
WordPress installation page is displayed successfully (HTTP 200)
2) “POST /wp-admin/install.php?step=2 HTTP/1.1” 200 5176 “-” “curl/7.74.0”
Successful installation of WordPress
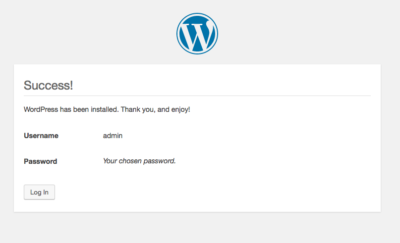
3) “POST /wp-login.php HTTP/1.1” 302 5 “-” “curl/7.74.0”
Successful login into WordPress dashboard
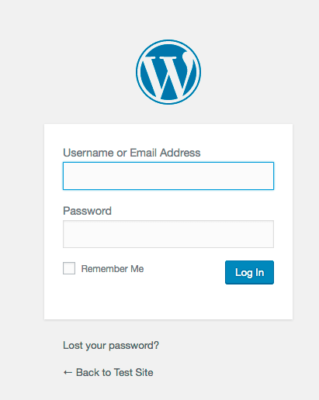
4) “GET /wp-admin/plugin-install.php?tab=upload HTTP/1.1” 200 26399 “-” “curl/7.74.0”
The page for manual plugin loading is selected
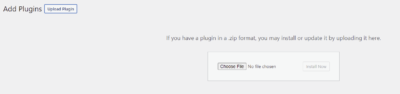
5) “POST /wp-admin/update.php?action=upload-plugin HTTP/1.1” 200 17887 “-” “curl/7.74.0”
Form Maker plugin is installed
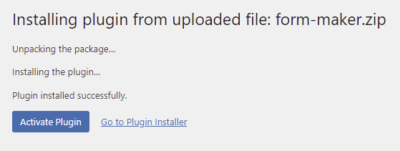
6) “GET /wp-content/plugins/contact-form-maker/contact-form-maker.php?a=0&b=930015466278503187 HTTP/1.1” 200 5 “-” “curl/7.74.0”
PHP shell is called using Form Maker plugin
7) “POST /wp-includes/.query.php HTTP/1.1” 200 40 “-” “Go-http-client/1.1”
PHP shell (.query.php) is copied to the wp-includes system folder
Looking at the times of the various steps, you can see that the attack started at 14:25:23 and ended at 14:25:28, which means that it only took 5 seconds to hack the site!
For those of you that are used to deal with hacked sites, you will have already understood that this hack is the “WPsetup attack” that has been around for many years.
What to do if you have been affected by this attack
1) Block hacker’s IP address
The first thing to do is to block access to the site and possibly to the server itself, from hacker’s IP address.
At site level you can do it using the .htaccess file (if you are using Apache webserver) or the site’s configuration file (if Nginx). At server level, you need to add a deny rule into your firewall (WAF, cloud firewall oor system firewall IPTables or ufw).
2) Move infected file
Using SSH or FTP access, move (don’t delete it!) the file to a folder on your laptop. It is a good idea to keep a copy of the file as evidence in case you would need to send it it to a legal authority.
3) Reinstall WordPress
In such cases it is recommended to reinstall WordPress. If you have SSH access to the virtual server, use the WordPress command line (wp-cli). If you don’t have SSH access, download WordPress to your laptop, unzip the file, and replace via cPanel or FTP, all the WordPress system files (root folder files, wp-admin and wp-includes folders. DON’T replace wp-config.php as it has the database configuration settings of your site).
4) Run a malware scan
After reinstalling WordPress, run a malware scan via a security plugin (Wordfence, Sucuri, Ninja malware, etc.) and also from Sucuri site check (https://sitecheck.sucuri.net)
5) Keep a copy of log files
Via SSH access or by requesting it from your hosting provider, make a copy of the web server log files (Apache, Nginx or other).
6) Report the incident
Using the command whois hacker_IP you should find out the Maintainer of the IP address. In the output you will find the email address to use in these cases (abuse@maintainer's_domain).
Write an email message reporting the incident including technical details (especially log files). Looking up on the Internet, you should find templates to use for this matter.
In case the hacked site is owned by an European company, General Data Protection Regulation (GDPR) requires that the incident is reported to the competent national supervisory authority.
What to do to avoid being hit
WordPress setup
When installing WordPress always choose automatic installation (Softaculous as in cPanel or other administration panels).
If for any reason you prefer the manual installation (download the latest.zip file, unzip it and then connect to the site to start the installation wizard) I highly recommend you start using the command line of WordPress (wp-cli) that will allow you to automate the whole process.
If you really don’t want to get involved with yet another tool to learn, or you don’t have SSH access to your virtual server, BEFORE unzipping the installation file, create an .htaccess and save it in the root directory of your site.
Inside the file, add the following directives:
deny from all
allow from YOUR_IP
Replace YOUR_IP, with the public IP of your Internet router (you can find it by connecting to this site: http://ipinfo.io/ip
Once the installation is finished, don’t forget to delete the blocking directives from the .htaccess file!!
Conclusions
After this thorough analysis, I contacted the sysadmin once again and told him about my findings. Then it came to his mind, that during the automatic installation of WordPress he hadn’t entered the right credentials to access the database, and when trying to open the site’s homepage, a database error was showing up.
The time needed to update database settings in the wp-config.php file (less than 1 minute…) were enough for the site to be hacked!!
So to recap, try as much as possible to install WordPress automatically and above all I will never get tired of repeating this: monitor your site continuously!