When WordPress is installed, a system administrator user is created, whose credentials are saved in the wp-users table of the WordPress database.
If you check into wp-users table, using mysql command line or phpmyadmin, you will see that the plain text password entered for the administrator user has been replaced by a sequence, starting with a 4 character pattern ($P$B), of numbers, letters and random characters.
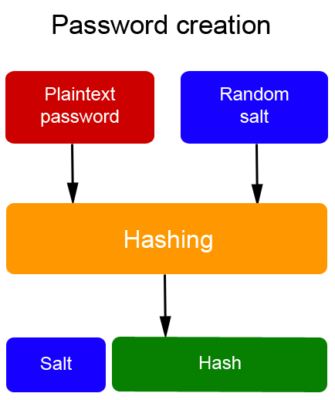
Saving the user’s password in the database
At the time of user’s registration, the password is combined with a random sequence of 64 characters called “salt” to then be processed by a hashing cryptographic procedure and finally saved in wp-users table along with user’s name and other additional data.
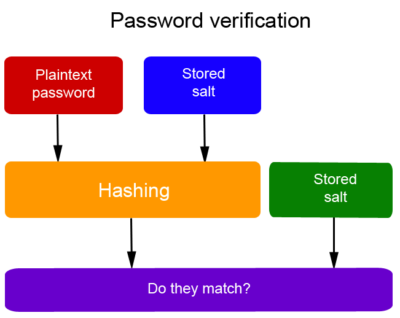
Password verification at login
During login procedure, password entered by the user is combined with the salt stored in the database, then processed by a further hashing procedure and the result is compared with the hash stored in the database.
If the sequences match perfectly, access to system is granted, otherwise it is denied.
Hash type
The hash function is a cryptographic function capable of mapping a random string (character sequence) into a new string of predefined length.
One of the most important peculiarities of this function, is the irreversibility, i.e. the inability to trace the initial string from the final string, unlike the encryption that allows you to trace the initial text through the use of cryptographic keys (public and private).
To produce hash strings, it is necessary to use cryptographic algorithms.
WordPress system uses, since the first versions, the MD5 algorithm (Message Digest 5) invented by Prof. Ronald Rivest of MIT in 1991.
However, today the MD5 algorithm is no longer considered safe, since in 2004 Chinese researchers managed to obtain a “collision” (when different strings produce an identical hash) making the algorithm no longer totally safe.
To strengthen the vulnerabilities of the MD5 algorithm, WordPress developers from version 2.5 (March 2008) onwards, included a password management framework (Portable PHP Password Hashing Framework, developed by Openwall) that uses MD5 algorithm, combined however with a 64 characters salt and a greater number of iterations or rounds (8) during hashing process.
Hash structure analysis
As an example we take the following hash:
$P$BXox1.zpleKOuW4jFS6/Fmg4iaiK.B/
The first 2 characters ($P) are the type of hashing algorithm used (in the case of WordPress it is MD5)
The 3rd and 4th characters ($B) are the number of iterations performed (in the case of WordPress they are 8,192).
Then there is a sequence of 30 characters, of which the first 8 (BXox1.zp) are a random salt and finally the last 22 characters are the hash (leKOuW4jFS6/Fmg4iaiK.B/).
How to further improve password’s security
Today, among the most secure algorithms, there are two algorithms: bcrypt (derived from Blowfish, used by default in Unix-like BSD systems), and Argon2 considered more secure than bcrypt.
In WordPress plugin’s repository, there are a few plugins that allow you to implement more secure algorithms such as bcrypt (Plugin tag: bcrypt)
A recommended plugin is Password Evolved (by developer Carl Alexander).
Further readings
1) Read from my Blog “How to create hack-proof passwords“
2) “Evaluation of password hashing schemes in open source web platforms“
Department of Digital Systems, University of Piraeus, Piraeus, Greece
23 July 2018








