As seen in my previous post How secure is the WordPress password algorithm?, the WordPress password framework, uses the MD5 algorithm along with a 64-character random sequence.
This sequence is called “salt” and is a technique used to strengthen the integrity of WordPress passwords as MD5 algorithm is not enough to guarantee the inviolability of WordPress passwords.
Salt & Keys
In the configuration file wp-config.php there is a section called “Authentication Unique Keys and Salts” where both salts and keys are saved.
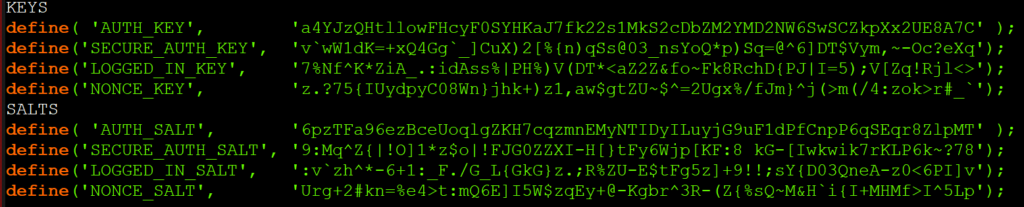
A. Keys (4 strings)
Keys are automatically generated during WordPress setup and are saved both in the database and in the wp-config.php configuration file.
The first 3 are used for the generation of cookies (for an explanation on cookies see the next section) and the last one for the generation of nonce (for more information see WordPress Nonces on WordPress.org).
a) AUTH_KEY
Key used to generate an authorization cookie to provide access to the administration panel for an user who is connecting to the website through an unprotected channel (http protocol).
b) SECURE_AUTH_KEY
Same type as the previous key, but this time for connections via an SSL protected channel (https protocol).
c) LOGGED_IN_KEY
Key used to generate a cookie for a user accessing the system. This type of cookie does not allow changes to be made to the system.
d) NONCE_KEY
Key used to generate a nonce token (“number used once”). The key itself is generated by concatenating the user ID + the parameter $action + current date/time (timestamp).
The nonce token is used to uniquely identify requests to the site. This way, when the site receives a remote request, it is checked if there is a nonce token or not. If the token is not available the request is rejected, if it is available, the value of the nonce token is compared with the one saved in the system, if the nonce token matches then the request is accepted otherwise rejected with a 403 (Forbidden) error.
Example (deletion of a post’s comment):
https://www.example.com/wp-admin/comment.php?c=16570&action=deletecomment&_wpnonce=389c3b47b9
B. Salts (4 strings)
Salts are generated from the keys created during WordPress setup and are saved in the wp-config.php configuration file.
During hashing operations, salts are linked to keys to reinforce hashes created during the various authentication and authorization operations performed by the system.
a) AUTH_SALT
String added to the corresponding AUTH_KEY key to generate a hash for the creation of an authorization cookie.
b) SECURE_AUTH_SALT
String added to the corresponding SECURE_AUTH_KEY key to generate a hash for creating the authorization cookie.
c) LOGGED_IN_SALT
String added to the corresponding key LOGGED_IN_KEY to generate a hash for the creation of the system access cookie.
d) NONCE_SALT
String added to the corresponding NONCE_KEY key to generate a hash for the creation of the protection token.
Cookies
Unlike other systems based on PHP language, which use PHP sessions to manage user authentication, WordPress manages authentication through a cookie-based system.
There are 4 cookies created by WordPress:
1) wordpress_[hash]
When you log in, a first cookie is created where user’s authentication specifications are stored. This cookie is used to access the administration dashboard for connections through an unprotected channel (http).
2) wordpress_sec_[hash]
The same functionalities as the above mentioned cookie, for connections through an SSL protected channel (https).
3) wordpress_logged_in_[hash]
After logging in, a second cookie is created with the user’s identity specifications and the login time.
4) wp-settings-{time}-[UID]
A cookie used to customize the administration dashboard interface.
Cookie structure
Example of authentication cookie structure (AUTH_COOKIE)
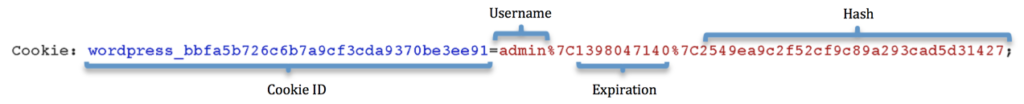
a) Cookie ID
The ID cookie is generated by concatenating the string “wordpress_” + hash generated by the MD5 hashing of the site’s url
(see WordPress source code ver. 5.2.3)
b) Username
The user name registered in the system
c) Expiration
Cookie’s expiration date and time (default duration 48 hours) in Unix timestamp (Wikipedia) format
d) Hash
This is a HMAC hash type (hash-based message authentication code – Wikipedia).
In a first step, the hash is generated by an MD5 value of the user name combined with the expiration date of the cookie.
Then a second hash is generated with the user name, the expiration date and 4 characters of the user password hash.
Finally, in a third step, the strings AUTH_KEY and AUTH_SALT are concatenated, which are then passed to the function wp_hash, to generate the final hash.
(see WordPress source code ver. 5.2.3)
What are the risks?
The most obvious risk is that a malicious user may come into possession of your cookies to access your WordPress administration dashboard.
Such attacks are carried out by redirecting requests made by a remote user’s browser to a malicious site, created specifically to take possession of the cookies on the user’s computer.
Another equally obvious risk is the possibility that a malicious user may get possession of the “salt & keys” of your wp-config.php file.
From the “salt & keys”, it is possible to create in a short time, a healthy cookie with which you may have free access to the administration dashboard with administrator rights! (“cookie forging”).
How can I protect my website?
1) SSL certificate
The first level of protection is the SSL certificate, which thanks to the encryption of data exchanged between the web server and the visitor’s browser, strengthens the system’s security by preventing any malicious users to intercept the flow of data and read its contents.
2) Enabling HSTS security header
Installing an SSL certificate on your site is of little help, if you do not enable the HSTS (HTTP Strict Transport Security) security header that forces visitors to the site to use only the encrypted HTTPS protocol to communicate with the web server.
For instructions on how to implement it in your site read my post on HTTP security headers
3) wp-config.php configuration file
a) set 644 permissions
b) Block access to the file , using htaccess directives
c) Set up login and access to administration dashboard only through SSL encrypted channel. To achieve this, enter the following directives into the wp-config.php file:
define( ‘FORCE_SSL_LOGIN’, true );
define( ‘FORCE_SSL_ADMIN’, true );
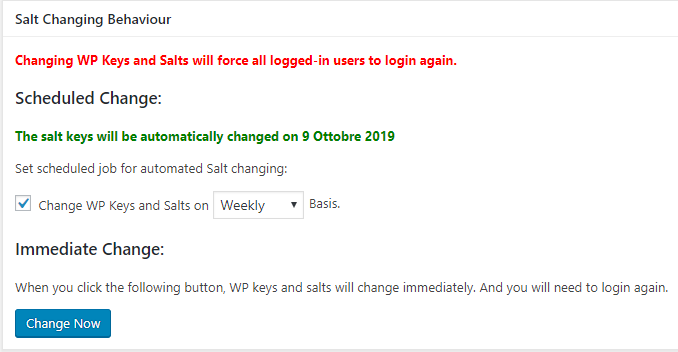
d) Change “salts & keys” regularly.
Changing salts & keys, can be done manually using the official app provided by WordPress at https://api.wordpress.org/secret-key/1.1/salt/ and then copying/pasting the new strings into wp-config.php file, or using a plugin that does all the work automatically!
Salt Shaker
This plugin, once installed, allows you to schedule an automatic replacement of salts & keys.